Dark Web: Potential Impacts on Network Infrastructure

Many of us have heard about the dark web, usually when talking about nefarious activities such as identity theft and the sale of illegal drugs. The dark web has gotten the reputation of a horror movie; an underground black market that exists to aid criminals in stealing information, selling narcotics and weapons, or “hackers for hire.” While much of this does happen, there are more complexities of the dark web than most realize. Research even suggests that the visible network is only about 4% of the entire internet!
The Surface Web
Thinking of the internet as an iceberg, at the very top we have the Surface Web. These are websites accessible to anyone with internet access, including this article. Common websites such as Google.com and social networking sites like Facebook and Instagram are considered The Surface Web. You do not need special programs or authorization to visit these websites.
The Deep Web
Not to be confused with the dark web, the Deep Web requires special permissions to access. This part of the internet is also quite common; with examples like your banking website or a secure file database like SharePoint. Academic resources, internal company services and government documents can also live in the Deep Web. These are sites blocked for search engine robots, so they cannot return results for pages requiring registration, payment, or passwords to access.
The Dark Web
The Dark Web is associated with websites, forums, and online shops that allow users to surf the web namelessly and without tracking. Despite its bad reputation, it’s estimated that roughly half of the Dark Web’s content is legal. So, when talking about the Dark Web it’s more accurate to say that it’s a place of anonymity, rather than crime. The initial idea behind creating the dark web by the U.S. Naval Research Lab in 1995 was to provide a place that guaranteed privacy when transmitting data. Users attempting to evade government censorship can share information on the Dark Web. Most notably and recently, when the COVID-19 outbreak began in Wuhan, China. Information about the virus was initially censored. Doctors could not speak publicly about the threat of the virus. They relied on being able to post updates on the Dark Web, knowing it would be nearly impossible for the Chinese government to trace the leaked information.
Network Infrastructure and Security
Understanding network infrastructure is crucial for navigating the complexities of both the Deep Web and the Dark Web. Network infrastructure refers to the underlying hardware and software that supports internet connectivity and data exchange. A well-designed network infrastructure ensures secure data transmission and prevents unauthorized access. When considering Dark Web monitoring and protection, it’s essential to evaluate how your network infrastructure can be fortified against potential threats. A robust network infrastructure will include firewalls, intrusion detection systems, and secure access protocols to protect against breaches that could expose sensitive information on the Dark Web.
Early Detection is Key
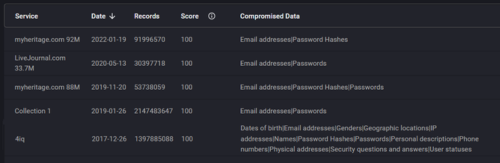
Keeping this in mind, it is still important to understand the importance of a Dark Web scan, not just in the office for your professional accounts but your personal accounts as well. As of April 2023, cybercriminals could purchase the details of a credit card with a $5,000 balance for just $110. Antivirus and malware programs are no longer enough, these services can prevent malicious files from infiltrating your system, but once that information is compromised – that’s it. So, who should be doing Dark Web scans? The simple answer is everyone, but there are certain industries that are more vulnerable than others. The five industries most targets by hackers are:
- Education and research
- Finance and insurance
- Healthcare and pharmaceuticals
- Public administration
- Retail
With the increase in reliance on digital platforms for day-to-day operations, cybersecurity is quickly becoming a fundamental part of any organization’s strategy. By scanning the Dark Web on a regular basis, you can identify potential breaches early on and mitigate them quickly. If your Dark Web scan detects compromised credentials, it is recommended that you do the following as soon as possible:
- Change the compromised password for the breached account to something more complex, using a combination of numbers, capital and lowercase letters and symbols.
- Updating any passwords that were similar on other accounts.
- Pay close attention to future communications appearing to come from the breached service for possible impersonation attempts by cybercriminals.
- Keep an eye on your credit cards and banking accounts for any suspicious activity.
Dark Web Monitoring Service Provider Shopping
If you’ve never been Dark Web monitoring service provider shopping (and most have not!) you may not be too sure what to look for. These services are becoming increasingly popular so knowing what features to look for can help you make the best choice for you and your business. Here are some things to consider:
- Comprehensive coverage – ensure the provider you’re looking for indicates a wide range of sources on the dark web. Private sites, forums and online shops should be noted as well as what type of data you can expect to uncover. Will it be able to detect only compromised passwords or will it also uncover other sensitive data such as emails, addresses, social security numbers, etc.
- Fast alert system – ask about turnaround time for notifications. These tools should alert you in real time as soon as any relevant threats are detected
- Cost – evaluate the cost of dark web solutions against their benefit and ensure you’re getting the best buy for your buck by reading reviews or consulting with peers.
- Quality and Quantity – the information you’re getting from these tools should be accurate and current. They should be able to distinguish between false positives and genuine threats so you can respond accordingly. It should also grow and change with your business. As you continue to evolve, the service provider should be able to accommodate more data and refine their process as the threats become more frequent and sophisticated.
- Business Models - Some IT providers offer options popular with IT Managers and Business Owners alike. Not every business needs to be fully managed, but benefit from staying involved with resources they need, or augmenting their knowledge base. Co-Managed Services work best for those organizations. Fully Managed IT Services are for those companies that prefer a hands-off solution with a fully outsourced IT management solution.
- Industry Knowledge & Services - In addition to being highly responsive and communicative, IT providers should possess extensive knowledge in cybersecurity and be skilled not only in quickly and thoroughly resolving issues but also in proactively safeguarding networks from potential vulnerabilities. Read more on our page about Cyber Security Managed Services.
Dark web scanning is just one layer of cybersecurity, but it’s one of the most important. The Dark Web is a little grayer when you look at it’s current use and abuse. By understanding what it is and what it’s used for you can improve your security stack and protect your assets, reputation, and customer trust.


